Understanding cybersecurity assessments
Cybersecurity assessments are evaluations that help identify and improve security vulnerabilities in a company’s digital systems. They aim to measure the effectiveness of existing security measures and recommend improvements to protect against cyber threats. During assessments, experts analyze different aspects of a company’s digital infrastructure, such as network security, data protection, and threat detection. The findings from these assessments help organizations strengthen their defenses and safeguard sensitive information from potential cyber attacks.
![]()
Importance of cybersecurity assessment services
Cybersecurity assessment services are vital to ensure your digital information stays safe from cyber threats. These services help identify weak points in your system that hackers could exploit. Regular assessments can pinpoint vulnerabilities before an attack occurs, allowing you to strengthen your defenses. Cybersecurity assessment services provide a proactive approach to safeguarding your sensitive data and maintaining the trust of your customers.
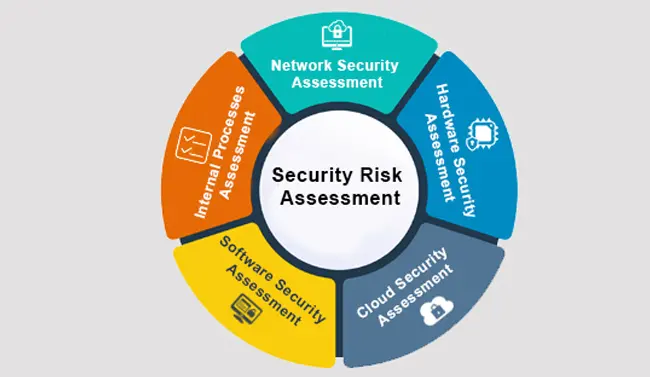
Types of cybersecurity assessments
There are a few types of cybersecurity assessments that companies often utilize. These assessments help identify potential security risks and vulnerabilities in your systems. Some common types include:
- Vulnerability Assessment: Identifies and quantifies vulnerabilities in your systems.
- Penetration Testing: Simulates a real attack to test the strength of your defenses.
- Security Audits: Evaluates the overall security of your systems and processes.
Each assessment has its own focus and purpose, so it’s essential to choose the right one based on your specific cybersecurity needs.
Benefits of conducting cybersecurity assessments
When you conduct cybersecurity assessments, you can identify vulnerabilities in your system before cyberattacks happen. This can help you strengthen your security measures and protect your sensitive data. Additionally, conducting assessments regularly can help you stay compliant with industry regulations and standards. Regular assessments can also improve your organization’s overall security posture and reduce the risk of costly data breaches.
How to choose a cybersecurity assessment service provider
When selecting a cybersecurity assessment service provider, look for a reputable company with experience in cybersecurity. Make sure they offer a variety of services tailored to your needs. Check for certifications such as CISSP or CISA to ensure their expertise. Ask for references from past clients to gauge their track record. Compare pricing structures and service offerings to find the best fit for your business.
Steps involved in a cybersecurity assessment
Cybersecurity assessment services involve several key steps. Firstly, the assessment begins with identifying and evaluating potential security risks and vulnerabilities within your organization’s systems. Next, analyzing current security measures in place is crucial to understand any gaps that need addressing. Testing the security systems to ensure they are effective is also a critical step. Finally, providing recommendations and creating a plan to enhance overall cybersecurity defenses are essential parts of the assessment process.
Tools and techniques used in cybersecurity assessments
Cybersecurity assessment services commonly use a variety of tools and techniques to evaluate the security of an organization’s digital systems. Here are some of the key methods used:
- Vulnerability Scanning: This involves scanning networks and systems for known vulnerabilities that could be exploited by attackers.
- Penetration Testing: Also known as ethical hacking, this simulates real-world cyber attacks to identify weaknesses in a system’s defenses.
- Security Audits: These thorough examinations assess an organization’s security controls, policies, and procedures to ensure they meet industry standards.
- Risk Assessments: This evaluates potential risks to an organization’s digital assets and helps prioritize security efforts based on the level of risk.
By employing these tools and techniques, cybersecurity assessment services can pinpoint weaknesses and recommend improvements to enhance an organization’s overall security posture.
Common vulnerabilities identified in assessments
During cybersecurity assessments, some common vulnerabilities that are often identified include weak passwords, unpatched software, lack of secure coding practices, and inadequate network security configurations. Weak passwords are a common way hackers can gain access to systems easily. Unpatched software leaves systems vulnerable to known exploits that have not been fixed by updates. Lack of secure coding practices can create vulnerabilities in software applications that hackers can exploit. Inadequate network security configurations can lead to unauthorized access to sensitive data. It’s crucial for organizations to address these vulnerabilities promptly to enhance their overall cybersecurity posture.
Responding to findings from a cybersecurity assessment
After a cybersecurity assessment, it is important to address any findings promptly to enhance your digital security. This involves implementing the recommended changes and fixes identified during the assessment. To respond effectively:
- Prioritize addressing the critical findings first to mitigate any potential high-risk vulnerabilities.
- Collaborate with your IT team to implement the necessary security measures in a timely manner.
- Ensure regular communication with your cybersecurity assessment service provider for guidance and support.
- Conduct regular follow-up assessments to monitor the effectiveness of the implemented changes and to stay proactive against emerging threats.
Ensuring continuous cybersecurity improvement
To ensure that your cybersecurity stays strong, it’s important to regularly assess and improve it. Cybersecurity assessment services help you identify weaknesses in your systems, detect potential threats, and strengthen your defenses. These services provide a comprehensive evaluation of your cybersecurity posture, outlining areas that need attention and providing recommendations for enhancement. Regular assessments are crucial to staying ahead of cyber threats and keeping your data safe.